Daniel Nelson, Armstrong Teasdale partner and Certified Ethical Hacker, shares insights about vulnerabilities all companies face.
 |
Nelson, who is also a Certified Information Privacy Professional, shared his tips at the ECN (Employers Counsel Network) Annual Conference, held recently in Seattle. (ECN is the network of attorneys from all 50 states that write BLR’s state compliance newsletters.) Reporting provided in part by Celeste Blackburn, BLR Editor.
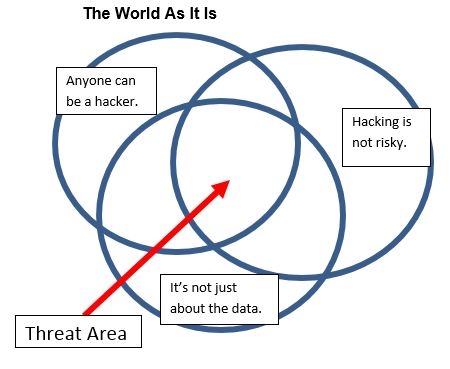
Many people think of information security compromise as the work of hackers, offshore data thieves, and other external threats, says Nelson. But, as Pogo once said, “We have met the enemy, and he is us.” The vast majority of security events are inadvertent or sometimes intentional “inside jobs.” If your organization experiences compromise, it most likely will be caused by an employee, not an external actor.
The Tools and Knowledge Are Readily Accessible
Although we would like to think that hacking is an arcane skill, in fact, hacking tools are readily available. “YouTube is Hacker University,” Nelson says. There are thousands of hacking tutorials there.
Nelson pictures the situation this way:

Looking to use software to ease your payroll headaches? Start on Wednesday, June 17, 2015, with a free interactive webcast from Kronos, How to End Service Bureau Fees, Reduce Costs, and Control Your Own Payroll Process. Learn More
Berkley Blue and Oaf Tobark

Two early hackers, known then as Berkley Blue and Oaf Tobark, are now better known as Steve Wozniak and Steve Jobs. Their hack? A box that hacked the phone system to allow free long-distance calls.
Nelson shared some basic information about hacking and hacking tools.
Hacking or Sport
Hacking is not just about getting data like Social Security numbers. People hack for sport—just like people play golf, fish, or hunt. They are looking for an adrenaline high.
They do hack for data, but also for:
- Revenge (disgruntled employees and former employees)
- Information (strategic plans)
- A Cause (activist)
- Street cred (within the hacker community)
- Boredom
- “Because it’s there”
The right payroll system can be faster, more accurate, and easy on your bottom line. Join us for a free interactive webcast, How to End Service Bureau Fees, Reduce Costs, and Control Your Own Payroll Process. Register Now
If they do go after data, they might be after:
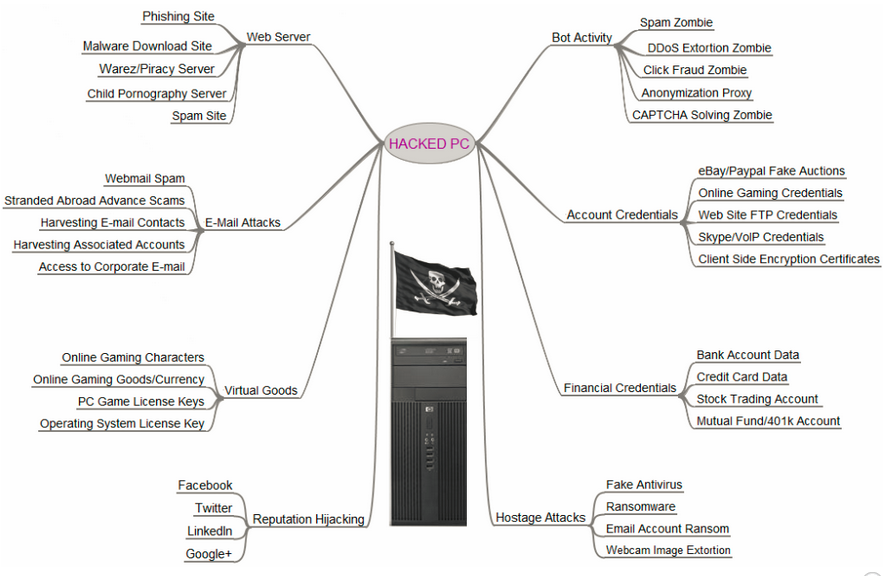
Brian Krebs, KrebsonSecurity.com
The tools and the knowledge needed to hack are easily accessible. Far more hacking is going on than you hear about.
There are a lot of open-sourced (free and available to the public) software and tools that are updated more frequently than Microsoft updates their products. Hacking isn’t so much about writing code as picking the right tool from the free open-sourced toolbox.
Many of the programs are menu-driven, click-the-box programs that “melt” after use or change their creation data, says Nelson.
In tomorrow’s Advisor, more from Nelson on Trojans and Onion Routers, plus an introduction to the free interactive webcast from Kronos, How to End Service Bureau Fees, Reduce Costs, and Control Your Own Payroll Process.

Eye-opening and alarming!